With a shift to a zero-trust and internet-based architecture for IT infrastructure, the entire Hitachi Group will achieve a safe and secure IT environment for both its employees and businesses.
Business will expand through the introduction of new ways of working and the adoption of cloud services.
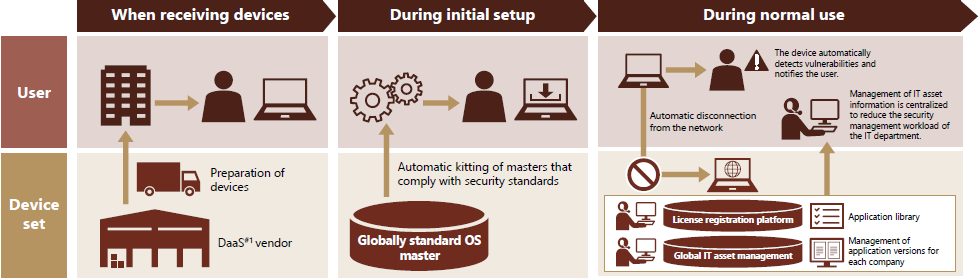
By developing device sets equipped with features such as automated device procurement, automated kitting, and network connection restrictions, we aim to enhance security further by globally deploying devices and software that comply with Hitachi Group's security standards.
We aim to enhance security and standardization by globally deploying a system that automatically kits devices and software in a manner compliant with Hitachi's security standards, ensuring that Hitachi Group employees can work securely and confidently without worrying about security threats.
Previously, each company was required to handle the detection, notification, and individual responses to vulnerabilities if end users continued using devices in risky conditions. The new system under development restricts device connections to networks prone to security incidents. This allows employees to work without concerns about security risks.
To ensure that Hitachi Group employees can engage in their work with peace of mind even when transferred between workplaces or sites, we aim to consolidate and globally manage the detection and mitigation of security vulnerabilities. Previously such tasks were handled individually by each company's IT department.
By providing globally unified security services, we are standardizing security levels across all companies to prevent the occurrence of security incidents.
If an information security incident occurs or there is a risk of such an incident, we check the usage status of the applications with vulnerabilities and take corrective measures to prevent the applications from starting.