With a shift to a zero-trust and internet-based architecture for IT infrastructure, the entire Hitachi Group will achieve a safe and secure IT environment for both its employees and businesses.
Business will expand through the introduction of new ways of working and the adoption of cloud services.
In the world of the internet, where cyberattacks are becoming increasingly sophisticated and skillful year after year, we are engaged in efforts to achieve safe and secure IT environments for both our employees and businesses throughout the entire Hitachi Group, in order to grow our businesses by introducing new ways of working and adopting cloud services.
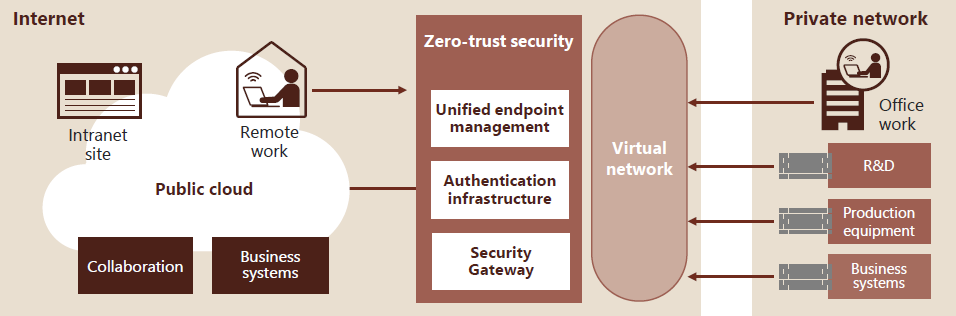
The Hitachi Group is moving forward with a transition to an architecture based on zero-trust security to enable employees to work securely anytime and anywhere.
We have completed the cloud migration of the zero-trust infrastructure, including endpoint management systems, authentication platforms, and proxy and remote access systems, enabling seamless access to our internal and external systems. Additionally, for systems where uniform cloud migration and security measures are challenging, such as production equipment and R&D environments, we have implemented network segmentation and access control between network segments.
Moving forward, we will continue to promote further cloud lift and shift of on-premises systems that remain in-house and expand security measures for our business systems.
Various business systems exist within the company, including production equipment and R&D environments. While micro-segmenting the network helps mitigate the spread of ransomware and other risks, it also contributes to the complexity of the network configuration and an increase in the management workload due to the addition of firewalls. Additionally, business systems are often built individually to meet specific requirements, making it challenging to implement common internal IT measures.
To address these challenges, we are enhancing network virtualization to create a more flexible and simplified network, thereby reducing management costs. Moreover, by expanding security measures for business systems, we aim to facilitate the rapid establishment of DX#1 and IoT#2 environments.
IT infrastructure to achieve zero trust security