Throughout the entire Hitachi Group, including companies in business reorganizations and companies integrated as a result of M&As, we are working to ensure compliance and business continuity for internal IT.
To respond to the risk of information leaks and increasing cyberattacks, as well as to ensure proper use of software, we are continuing our efforts to strengthen our IT controls.
With respect to large-scale earthquakes (such an earthquake is said to have a high probability of occurring in Japan in the near future) and natural disasters arising from global warming, as well as various other kinds of emergencies, such as pandemics and cyberattacks, we are formulating and operating IT-BCPs that enable us to support business continuity for the Hitachi Group through IT.
In addition, we are continually revising our plans so that we will be able to support next-generation IT architecture such as zero-trust security and cloud lift & shift.
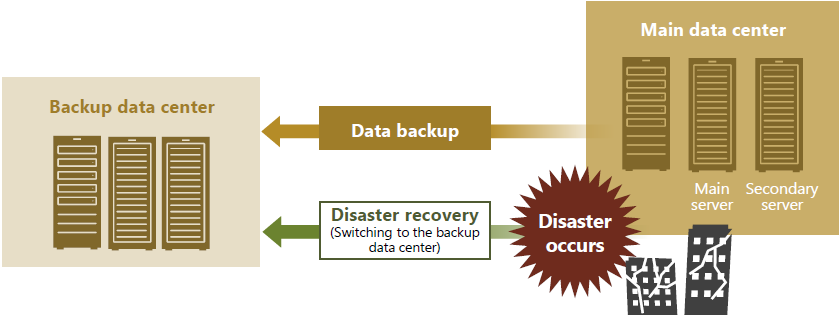
In preparation for large-scale disasters, we install and operate our servers in robust data centers, and select clouds that can enable us to continuously provide services if a disaster occurs. Also, we have set recovery time objectives for each service and defined disaster prevention levels accordingly. In addition, we are working to preserve data by establishing environments for secondary servers and data backups. For services that are important for business continuity, we have configured systems in multiple data centers and on clouds, and established early recovery mechanisms for disasters. Also, to prepare for emergency situations, we regularly conduct training in line with the BCP (Business Continuity Plan).
In response to new work styles and the expansion of cloud usage, we established and improved our remote work environment. By using the remote work environment, we are able to continue our business even in the event of a pandemic. In addition, we defined priorities for necessary system operations according to the degree of impact on the social function maintenance business and created operation plans.
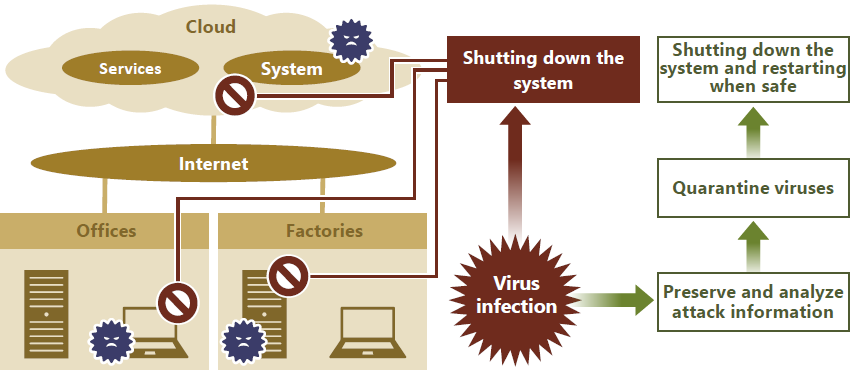
To combat cyberattacks, we are taking robust security measures by shifting to an architecture based on zero trust security. In anticipation of cyberattacks such as ransomware, targeted email attacks, worm-type viruses, and unauthorized access to servers open to the public, we have prepared response methods, from initial action to recovery, that are tailored to each type of attack. For example, these methods include isolating infected systems by shutting down the systems and suppressing the startup of applications, preserving and analyzing attack information, quarantining viruses, and shutting down the systems and restarting them when safe. We are working hard to ensure safe system operation and rapid recovery.
Furthermore, to firmly establish and improve our BCP, we regularly review our measures, for example, by conducting training in line with anticipated cyberattacks and modernization of our IT infrastructure, and by preparing for new threats.