Information Security
- Approach to Information Security
- Information Security Policy
- Framework for Promoting Information Security
- Information Security Management
- Cyber-Security Initiatives
- Data Protection Initiatives
- Third-Party Evaluations and Certifications
Approach to Information Security
Approach & Policy
The progress of digitization has brought new opportunities for creating value, but this progress also amplifies the risks that businesses face, including information leaks and operational disruptions caused by evolving sophisticated cyberattacks that impede business continuity. To minimize these risks, risk management related to information security has become one of the most crucial challenges for companies. Against this backdrop, Hitachi, aiming to be a global leader in the Social Innovation Business, is engaged actively in information security initiatives. We recognize cybersecurity measures as a crucial management challenge that addresses both value creation and risk management. Since Hitachi consists of numerous companies, we are pursuing our businesses as a unified group, One Hitachi. In line with this business policy, we address information security as One Hitachi, as well, striving to establish optimal security measures and ensure a sense of unity and agility. To this end, we accelerate the security measures based on common initiatives in accordance with the overall Hitachi policy.
Information Security ReportInformation Security Policy
Approach & Policy
Hitachi has created an information security policy and established various rules and the promotion structure based on this policy. Hitachi promotes information security management with the rules and the structure in order to protect various information assets such as information entrusted to us by our customers, the systems that store that information, and the information systems that provide social infrastructure services.
Information Security Policy
- Formulating administrative rules for information security and ensuring their continual improvement
- Protection and ongoing management of information assets
- Legal and regulatory compliance
- Education and training
- Preventing incidents and taking action when they occur
- Ensuring business processes are optimized within the corporate group
Framework for Promoting Information Security
Structure
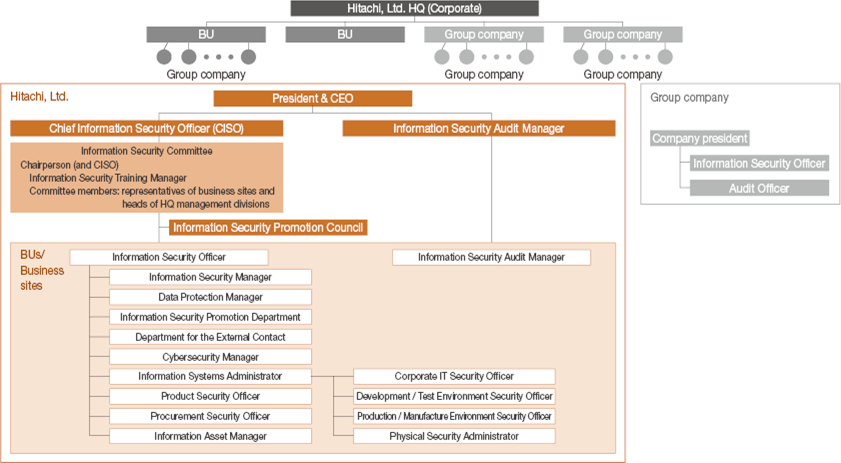
The Chief Information Security Officer (CISO) has overall responsibility and authority for implementing and operating information security and personal information protection, and oversees information security for all Hitachi products, services, and internal facilities. Chaired by the CISO, the Information Security Committee determines all policies and measures for information security and personal information protection. These policies and measures are announced to all Business Units (BUs), business sites, and group companies through channels such as the Information Security Promotion Meeting.
BUs and business sites operate their own information security divisions, with the head of the BUs or business sites serving as information security officers. These divisions implement information security management in each workplace and provide relevant education to employees. In response to the widening scope of potential cyberattack targets, we have also appointed officers who will be responsible for our internal IT environments, development & verification environments, production & manufacturing environments, and physical security environments such as office entry and exit points, all operating under the Information Systems Manager. In addition, in order to enhance the security of the products and services we offer our customers as well as that of supply chains, including those of our business partners, we have established the positions of Product Security Officer and Procurement Security Officer.
Group companies also implement information security frameworks, promoting groupwide information security through mutual cooperation. In fiscal 2023, we established new Information Security Departments directly controlled by corporate headquarter in the Americas, Europe, Asia, India and China in order to provide support to Hitachi Group companies in each of these regions and strengthen our global management.
Framework for Promoting Information Security
Information Security Management
Activities
Hitachi established a framework for information security management based on the ISO/IEC 27001 international standard. In light of the increasing severity of cyberattacks in recent years, we are strengthening our information security with the Information Security Standards which in compliance with the United States government standard SP800-171. The information security rules and the personal information protection rules including Information Security Standards have disseminated globally by Hitachi, Ltd. and group companies’ headquarters.
Preventing Information Leaks
Hitachi engages in a number of IT-related measures such as device encryption, secure PC use, electronic document access control and expiration processing software, ID management and access control via authentication infrastructure, e-mail and website filtering, etc. to prevent information leaks. In response to the proliferation of targeted e-mail attacks and other cyberattacks, we not only participate in an initiative to share information between the private sector and the government, but also strengthen various IT measures that include defense-in-depth strategy.
To prevent leaks from procurement partners, when outsourcing work that handles confidential information, we check and examine their information security measures based on Hitachi’s own standards in advance. We also provide tools to procurement partners for security education and for checking business information on computers. In addition, we require procurement partners to check and remove business information from personally owned devices.
Education on Information Security
Hitachi holds annual e-learning programs on information security and personal information protection for all executive officers and employees. The participation rate in Hitachi, Ltd. in fiscal 2023 was 100% (excluding those who could not attend due to personal leave, etc.). Besides, Hitachi, Ltd. offers a variety of programs depending on the target and aims, such as those for new employees, new managers, and lectures for information security manager. Training programs in Hitachi, Ltd. are shared with the group companies in order to actively implement training on information security and personal information protection in the entire group.
Hitachi also implements simulation training to educate employees about phishing attacks and other cyberattacks. Employees receive deceptive e-mails as phishing simulations to heighten their awareness of security through direct experience.
Information Security Management Evaluation and Monitoring
Hitachi implements information security and privacy protection initiatives based on the PDCA cycle of the information security management systems stipulated by Hitachi, Ltd. Hitachi conducts regular audits and inspections to monitor and evaluate whether management and measures for information security and data protection are implemented properly in each department.
Specifically, Hitachi works to reduce security risks by verifying the status of our information security measures through regular audits conducted by the audit departments, groupwide inspections, and regular on-site assessments carried out by a team of in-house security specialists.
All divisions of Hitachi, Ltd. and group companies in Japan conduct annual internal audits of information security and personal information protection. Internal audits at Hitachi, Ltd. are conducted independently by auditor appointed by the President & CEO. They are not allowed to audit their own divisions, which underlines our commitment to fairness and objectivity in auditing. The group companies in Japan conduct internal audits equivalent to Hitachi, Ltd., and all audit results are confirmed by Hitachi, Ltd.
Hitachi, Ltd. and group companies in Japan also contract with an external organization to conduct quarterly external vulnerability assessments of outside-facing servers.
In addition, all divisions of Hitachi, Ltd. perform annual self-directed checks of operations relating to personal information protection, and the divisions involved in operations that handle important personal information perform checks of each of these operations on a monthly basis. Through these measures, we regularly check the operational status of processes involving personal information.
Cyber-Security Initiatives
Activities
To address the risks posed by the increasing diversification of cyber-attack methods, origins, and impacts, Hitachi is expanding the scope of our security risk management which used to respond on measures for internal IT environments. Specifically, to reduce business risks going forward, we expanded the scope of risk management to include the development & verification environments and production & manufacturing environments which are used to create products & services, the supply chain and product & service development process.
Cyber-Security Management
Hitachi has established standards for internal IT environment-related vulnerability response measures and network security. We also require BUs and group companies to conduct regular status assessments of these measures and perform corrective actions. As a groupwide measure, we launched an initiative to monitor vulnerability mitigation for each device and follow up with users and administrators to expand the application of such measures.
In the development & verification and production & manufacturing environments, we established standards and guidelines for infrastructure construction and operations to ensure security compliance in each environment, and we pursue measures based on these guidelines within Hitachi Group. We also share information security requirement standards established by Hitachi with our procurement partners, working cooperatively to enhance security.
We have established management policies to address and maintain the security of products & services, and we follow measures based on these guidelines within the Hitachi Group. To allow us to carry out emergency responses in the event that a vulnerability is discovered or an incident occurs, we have established Product Security Incident Response Teams (PSIRTs, responsible for the technical aspects of product and service security) at our headquarters, BUs, and group companies. These teams cooperate to take appropriate action in response to vulnerabilities or incidents relating to our products & services.
In addition, we are building a framework, based on the Three Lines of Defense concept, that will keep security measures in place for our development & verification and production & manufacturing environments as well as our products & services. As the first line of defense, each BU and group company conducts self-assessments of whether they are in compliance with our guidelines and management policies. As the second line of defense, headquarters monitors the results of these self-assessments, a process which is in turn monitored by our audit divisions as our third and final line of defense.
Cyber-Security Monitoring
The Hitachi Security Operation Center (SOC) monitors security on an around-the-clock basis to ensure global-scale cyberattacks are detected and response measures initiated immediately. The Incident Response Team (IRT) collects and develops threat information and manages our response to any security incidents.
Today we see a wide range of cyberattacks, including supply chain attacks, zero-day attacks, and ransomware attacks. In this context, Hitachi strengthens cyber surveillance through Endpoint Detection and Response (EDR)*1 to monitor device behavior and perform authentication protection and External Attack Surface Management (EASM)*2 to harden the attack surface. We continue to improve and strengthen our cyber monitoring environment using the latest technology.
*1Systems to monitor suspicious behavior and respond quickly to attacks on endpoint devices such as computers.
*2Systems to identify and manage internet- and other external-facing assets that could be the targets of an attack.
Data Protection Initiatives
Activities
As digital technology continues to advance, the global trend toward leveraging data only accelerates. This situation has led to heightened interest in the protection of personal information and cross-border data exchange. In such an environment, Hitachi places significant importance on personal information protection initiatives to ensure the secure management of personal information received from customers and personal information involved in business operations. As a member of the global community, Hitachi is committed to protecting personal information in accordance with our vision for personal information protection, which is to provide safety and trustworthiness, and to value individual rights.
Personal Information Protection
Hitachi, Ltd. has established the Personal Information Protection Policy which is announced to all executive officers and employees, and is also publicly available. In addition, we have created a personal information protection management system based on this policy. This system ensures the protection of personal information by such means as appropriate management of personal information, educational programs for all employees, and periodic audits. We do not share personal information with third parties without data subject’s prior consent. Even in cases where prior consent is obtained, Hitachi requires the third party to whom the data is provided to comply with Hitachi’s Personal Information Protection Policy.
Hitachi also strives to safeguard personal information globally based on each company’s personal information protection policy, and we ensure that these companies comply with all applicable laws and regulations in each country and region, as well as to the expectations of society at large.
PrivacyMark Certification
Hitachi, Ltd. has obtained PrivacyMark*1 certification, which is a third-party certification of personal information protection. The entire Hitachi Group is committed to personal information protection, and 37 Hitachi Group companies in Japan have been granted the PrivacyMark as of the end of July 2024.
*1PrivacyMark: A third-party certification that is granted by Japan Information Processing Development Corporation, an assessment body, to businesses that have taken appropriate security management and protection measures related to personal information (invested by Japan Information Processing Development Corporation).
Privacy Protection Initiatives
In response to social demands for privacy protection measures, Hitachi aims to provide more appropriate and high-quality services and products, and to foster trust with consumers and other stakeholders, by balancing privacy protection and the use of personal data.
Since fiscal 2023, Hitachi, Ltd. has operated the Hitachi Privacy Impact Assessment (PIA) system, implementing privacy impact assessments for operations that involve handling of personal data and thereby putting in place measures to prevent privacy-related issues.
We are also approaching initiatives for privacy protection more proactively. Due to the nature of our Digital Systems & Services, which drive our digital business, we established within this sector the position of Personal Data Officer to oversee personal data handling and the Privacy Protection Advisory Committee, which consolidates our knowledge on privacy protection, supports risk assessments, and considers response measures.
Responding to Personal Data Protection Laws Around the World
With the increasing risk of privacy violations, lawmakers are actively seeking to create and modify relevant laws and legislation in countries and regions around the world. Hitachi ensures thorough global compliance with legal frameworks, continues to monitor related legal frameworks and social trends, and implements appropriate measures.
In Japan, Hitachi complies with the Amended Act on the Protection of Personal Information, and in the event that a leak may result in a situation that would harm the rights and interests of individuals, Hitachi promptly reports the leak to the Personal Information Protection Commission and notifies the affected individuals. In fiscal 2023, there were four recorded cases of personal information leaks at Hitachi, Ltd. based on the Act on the Protection of Personal Information. We identified the scope of the impact related to these cases and took appropriate action.
Hitachi also formulated a groupwide internal code of conduct concerning the protection of privacy, which takes into consideration international legal frameworks such as the European General Data Protection Regulation (GDPR). This code of conduct became effective as of April 2022. Moreover, individuals responsible for personal data protection are appointed in each group company, and support functions for regional group companies have been established within each regional headquarters. In this way, we ensure consistent personal information protection on a global scale.
Third-Party Evaluations and Certifications
Activities
Hitachi is promoting the acquisition of third-party evaluations and certifications for information security management. Our data centers and other divisions obtain certification from the ISMS Accreditation Center (ISMS-AC) in accordance with the ISO/IEC 27001 Information Security Management System international standard. Seven divisions at Hitachi, Ltd. have received this certification, and 25 divisions of 19 group companies*1 have also received this certification.
*1 As of the end of July 2024
Note:Hitachi normally refers to suppliers (including vendors and providers) as procurement partners, with whom we build business together on an equal footing